CISSP Certification: Ultimate Guide to Becoming a Certified Information Systems Security Professional

The cybersecurity landscape demands validated expertise, and CISSP certification stands as the industry’s definitive credential for security professionals. This comprehensive guide navigates the certification process, exam requirements, and career advantages specifically tailored for US-based security practitioners. Whether you’re aiming for CISO-level positions or strengthening your security architecture credentials, understanding the Certified Information Systems Security Professional […]
How to Build and Implement an Effective Business Continuity Program
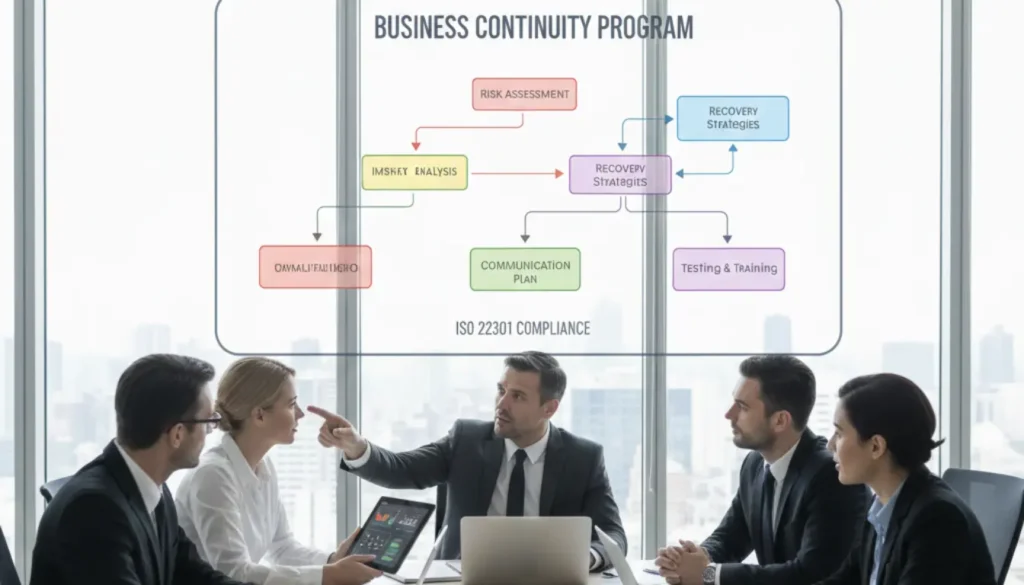
Modern organizations face unprecedented disruption risks—from cyberattacks to supply chain breakdowns. A robust business continuity program separates resilient companies from those that crumble under pressure. This guide walks you through proven methodologies for building scalable continuity frameworks, integrating AI-driven risk assessment tools that transform reactive planning into proactive resilience. Visit riskilience.com to audit your current […]
Business Continuity Certification Guide: CBCP, Training Programs & Career Development

Certified business continuity professional credentials represent the gold standard for business continuity expertise, providing practitioners with internationally recognized validation of their knowledge and competencies. As organizations increasingly recognize the strategic value of business continuity, demand for business continuity certification training and qualified professionals continues to grow across industries and geographic regions. This comprehensive guide explores […]
Certified Business Continuity Professional (CBCP): Complete Guide to Requirements, Exam & Career Benefits
The Certified Business Continuity Professional (CBCP) represents the premier global certification for business continuity professionals, offered by DRI International (Disaster Recovery Institute International). As the most widely recognized business continuity certification worldwide, CBCP validates comprehensive expertise in business continuity planning, implementation, and management across all industries and organizational types. This comprehensive guide provides everything you […]
ISO 27001 Business Continuity Requirements: Complete Guide to Annex A Controls & Implementation

ISO 27001 business continuity requirements represent a critical component of information security management that ensures organizational resilience and data protection during disruptions. While ISO 27001 primarily focuses on information security, its ISO 27001 business continuity requirements create essential linkages between security management and operational continuity. Understanding these requirements and their implementation is crucial for organizations […]
ISO 22301 Business Continuity Standard: Complete Guide to Requirements & Certification
ISO 22301 business continuity represents the international standard for business continuity management systems, providing organizations worldwide with a systematic framework for building, implementing, and maintaining comprehensive continuity capabilities. As the ISO business continuity standard 22301, it establishes requirements that enable organizations to protect stakeholders, reputation, and value-creating activities during disruptions. This comprehensive guide explores everything […]
Business Continuity Management Policy Guide: Development, Implementation & Best Practices

Business continuity management policy serves as the foundation for organizational resilience, providing the strategic direction and governance framework needed to build, implement, and maintain comprehensive continuity capabilities. A well-developed policy transforms business continuity from tactical emergency planning into a strategic organizational capability that protects stakeholders while enabling competitive advantages. This comprehensive guide provides everything you […]
Business Continuity Management Lifecycle: BCM Process Phases & Implementation
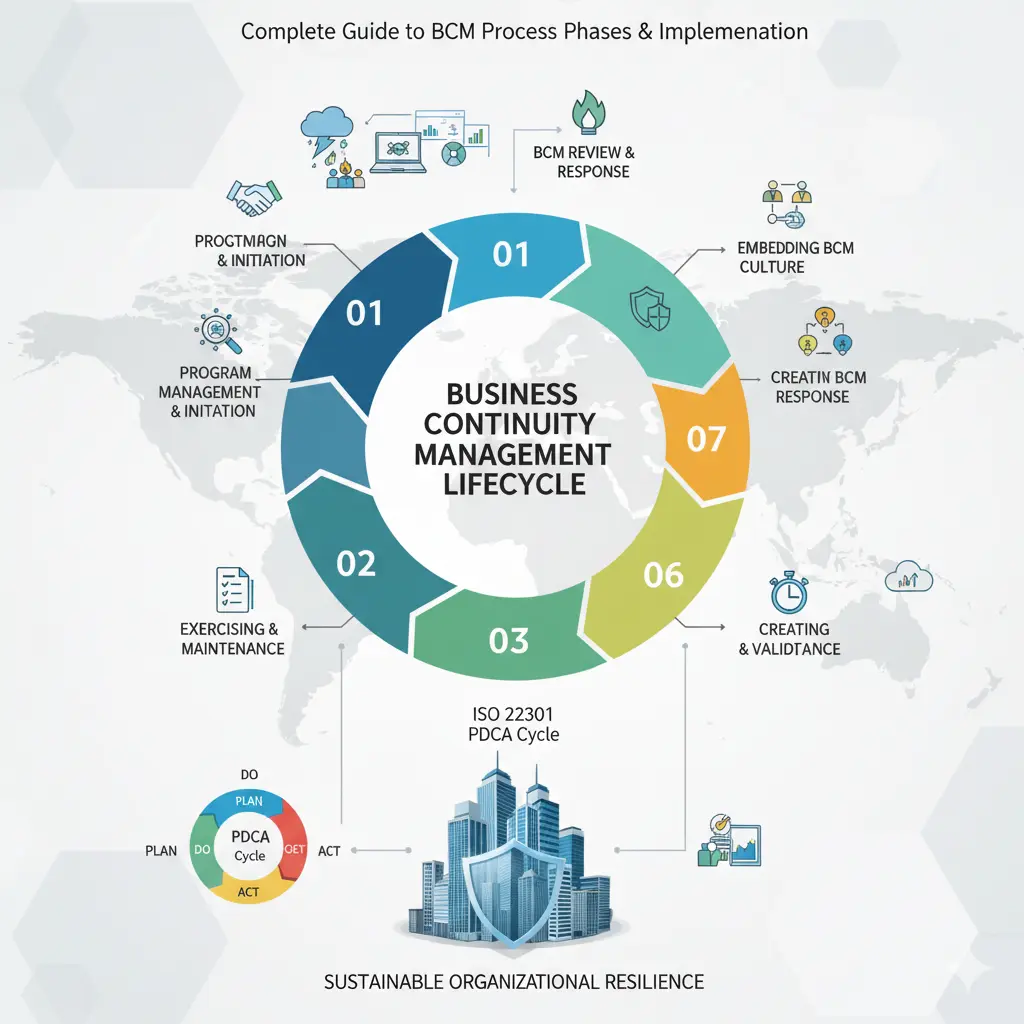
The business continuity management lifecycle provides a systematic approach to building, implementing, and maintaining comprehensive organizational resilience. Unlike one-time planning activities, the BCM lifecycle represents an ongoing process that continuously evolves to address changing organizational needs, emerging risks, and lessons learned from testing and real-world incidents. This comprehensive guide explores each phase of the business […]
Business Continuity Management Framework: Complete Guide to BCM Systems & Lifecycle
Business continuity management represents the strategic discipline that ensures organizational resilience through systematic planning, implementation, and continuous improvement of continuity capabilities. Unlike simple emergency planning, BCM business continuity management integrates continuity considerations into all aspects of organizational governance and operations. A comprehensive business continuity management framework provides the structure needed to build, maintain, and optimize […]
Business Continuity Management: Complete Guide to BCM Strategy, Implementation & Best Practices

Business continuity management represents a strategic organizational discipline that goes far beyond traditional emergency planning to create comprehensive resilience capabilities. As a holistic approach to organizational preparedness, BCM business continuity management integrates risk management, operational planning, and strategic thinking to ensure organizations can survive, adapt, and thrive through various disruption scenarios. This comprehensive guide explores […]
