Modern organizations face unprecedented disruption risks—from cyberattacks to supply chain breakdowns. A robust business continuity program separates resilient companies from those that crumble under pressure. This guide walks you through proven methodologies for building scalable continuity frameworks, integrating AI-driven risk assessment tools that transform reactive planning into proactive resilience. Visit riskilience.com to audit your current setup and get started with expert guidance.
Understanding Business Continuity Programs vs. Plans
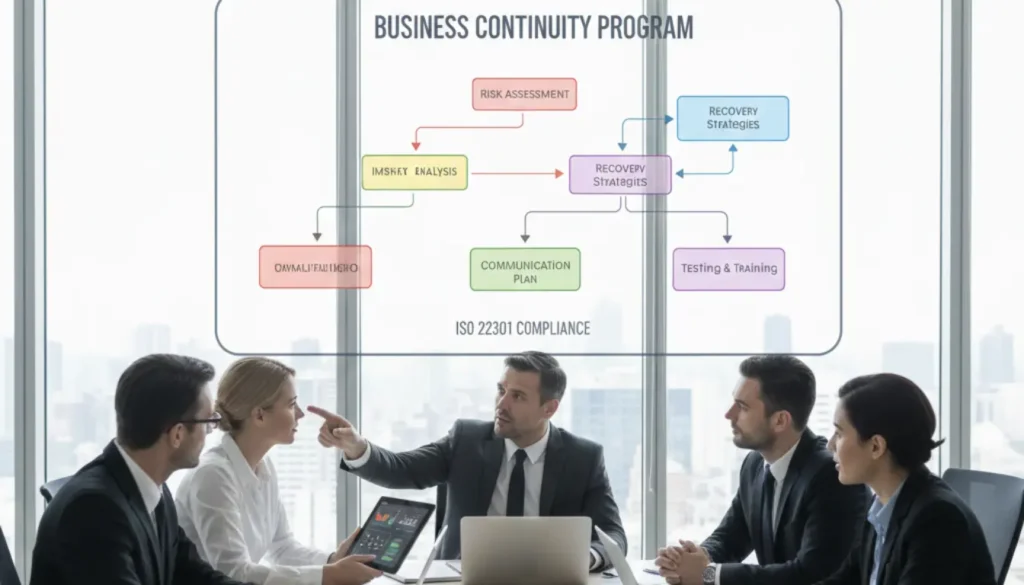
A business continuity program functions as an ongoing management system—think ISO 22301 compliance—that encompasses governance structures, systematic processes, and continual improvement cycles. Unlike static plans that merely document recovery procedures, programs establish living frameworks that evolve with your organization. They embed continuity thinking into daily operations rather than treating it as an afterthought pulled from a shelf during crises.
Programs ensure repeatability; plans alone fail without execution.
Key differences that matter:
- Programs include comprehensive BIA, ongoing risk assessment, and regular training; plans focus narrowly on recovery steps
- Programs drive measurable metrics and regular audits; plans risk obsolescence without systematic reviews
- Programs align with frameworks like ISO 22301 business continuity standards; plans may lack certification pathways
Step 1: Program Initiation and Management
Securing executive buy-in demands more than presentations—it requires demonstrating how business continuity management directly supports revenue protection, regulatory compliance, and competitive advantage. Establish governance through a steering committee with cross-functional representation, then codify your commitment in a comprehensive policy framework that defines roles, responsibilities, and escalation protocols. Your business continuity management policy becomes the constitutional document guiding all subsequent activities.
Identifying Risks and Vulnerabilities
Conduct initial risk evaluation to prioritize high-impact threats like cyber attacks or supply chain failures.
| Risk Type | Likelihood | Impact | Priority |
|---|---|---|---|
| Cyber Attack | High | High | Critical |
| Natural Disaster | Medium | High | High |
| Supply Chain Disruption | High | Medium | High |
| Key Personnel Loss | Medium | Medium | Medium |
| Pandemic/Health Crisis | Low | High | Medium |
Building Organizational Framework
Effective programs require dedicated resources and clear accountability structures:
- Appoint a BCM leader with executive access and assemble specialized teams (Crisis Management, Business Continuity, Disaster Recovery)
- Allocate realistic budgets for assessment tools, training programs, and recovery infrastructure
- Define reporting lines that ensure continuity considerations reach boardroom discussions
- Establish integration points with existing risk management and operational resilience initiatives
Schedule a risk assessment consultation at riskilience.com.
Conducting Business Impact Analysis (BIA) for Critical Processes
Business Impact Analysis quantifies what’s actually at stake when operations falter. Analyze five dimensions: financial losses (revenue, penalties), operational disruptions (throughput, capacity), customer impacts (satisfaction, retention), regulatory consequences (fines, sanctions), and reputational damage (brand value, market position). This analysis defines your Recovery Time Objectives (RTO) and Recovery Point Objectives (RPO) for time-sensitive processes—the guardrails that shape all subsequent strategy decisions.
Key BIA Components
Thorough analysis requires examining multiple interdependencies:
- Process dependencies and resource requirements including personnel skills, technology systems, facility access, and supplier relationships
- Downtime tolerance quantification measured in hours, transactions lost, or customer commitments missed
- Cascading impact mapping showing how one disruption triggers failures across connected processes
- Regulatory deadline identification highlighting compliance windows that cannot flex
BIA Best Practices for US Businesses
Use data-driven assessment tools to map dependencies accurately, particularly given US regulatory frameworks like NIST cybersecurity standards and sector-specific requirements (HIPAA for healthcare, SOX for public companies, GLBA for financial services). Regional considerations matter—hurricane preparedness differs vastly between Gulf Coast and West Coast operations.
Prioritize processes supporting revenue delivery.
Leverage riskilience.com’s AI BIA tool for faster insights.
Developing Recovery Strategies and Business Continuity Strategies
Recovery strategies balance cost-effectiveness against your defined RTOs and RPOs. Evaluate options systematically: data backups (onsite, cloud, hybrid), infrastructure redundancies (hot sites, warm sites, cold sites), alternate work locations (remote work, reciprocal agreements, mobile facilities), and supplier diversification. The goal isn’t building Fort Knox—it’s implementing cost-justified safeguards matched to actual risk exposure.
Technology and DR Integration
| Strategy | RTO | Cost | Complexity | Use Case |
|---|---|---|---|---|
| Cloud Backup | <4 hours | Medium | Low | Standard operations |
| Full Replication | <1 hour | High | High | Mission-critical systems |
| Warm Site | 4-24 hours | Medium | Medium | Balanced approach |
| Cold Site | 24-72 hours | Low | Low | Non-critical functions |
Vendor and Supply Chain Continuity
Third-party dependencies create vulnerability blind spots. Address them proactively:
- Assess vendor resilience through questionnaires, site visits, and contract provisions requiring continuity documentation
- Implement mutual assistance agreements with industry peers for resource sharing during regional disruptions
- Diversify critical suppliers across geographic regions to avoid single-point failures
- Monitor vendor financial health as bankruptcy creates immediate operational risks
Unique perspective: Incorporate AI predictive analytics for dynamic strategy updates. Machine learning algorithms can analyze threat patterns, resource availability, and cost fluctuations to recommend strategy adjustments before disruptions occur—transforming continuity from reactive to anticipatory.
Creating Your Business Continuity Plan Document
Your written business continuity plan translates strategies into actionable procedures addressing three core scenarios: facility loss, IT system failure, and personnel unavailability. Document precise roles (Incident Commander, Communications Lead, Recovery Coordinators), communication protocols (escalation trees, notification templates, status update schedules), and activation triggers (specific conditions warranting plan deployment versus normal incident response). Well-crafted business continuity plans eliminate ambiguity when clarity matters most.
Essential BCP Sections
Comprehensive plans address all critical elements:
- Emergency response steps covering immediate safety measures, damage assessment, and initial notifications
- Recovery timelines and checklists providing hour-by-hour guidance for the first 24-72 hours
- Resource inventories listing equipment, supplies, contact information, and access credentials needed for recovery
- Alternate process procedures explaining workarounds when primary systems remain unavailable
Crisis Communication Framework
Define pre/during/post-event messaging for stakeholders.
Communication determines whether disruptions become crises. Pre-event preparation includes template messages, approval workflows, and designated spokespeople. During incidents, establish update cadences (every 2 hours initially, then daily) for employees, customers, regulators, and media. Post-event communication covers restoration timelines, lessons learned, and preventive measures implemented—building stakeholder confidence through transparency.
Build your custom BCP with riskilience.com’s guided platform.
Training, Testing, and Exercises for Program Readiness
Documentation without capability equals false confidence. Roll out awareness programs ensuring every employee understands their continuity role, conduct tabletop exercises walking teams through scenarios without resource mobilization, and run full-scale simulations that test actual recovery procedures under time pressure. Regular business continuity plan testing builds muscle memory and validates whether plans actually work under stress.
Exercise Types and Schedules
| Exercise Type | Frequency | Duration | Goals |
|---|---|---|---|
| Tabletop Discussion | Quarterly | 2-3 hours | Identify gaps, validate roles |
| Functional Exercise | Semi-Annual | 4-6 hours | Test specific capabilities |
| Full-Scale Simulation | Annual | 8+ hours | Validate entire program |
| Component Testing | Monthly | 1-2 hours | Verify technical systems |
Employee Training Best Practices
Effective training goes beyond annual PowerPoint presentations:
- Role-specific drills ensuring recovery team members can execute their assigned responsibilities
- New hire onboarding integration introducing continuity expectations from day one
- Cross-training programs developing backup capabilities for critical positions
- Realistic scenario development using plausible disruptions rather than Hollywood-style disasters
- Measurement and feedback tracking participation, comprehension, and performance metrics
Maintenance, Audits, and Continual Improvement
Business continuity programs require ongoing stewardship, not one-time implementation. Review annually at minimum, or immediately following significant changes—mergers, new facilities, major technology deployments, regulatory shifts, or actual incidents. Track performance metrics consistently, assign corrective actions through management reviews, and document improvements to demonstrate program maturity. The business continuity management lifecycle never truly ends; it cycles through assessment, planning, implementation, and refinement.
Common Metrics to Track
Measurement drives accountability and improvement:
- Exercise success rate measuring objectives achieved during tests
- Plan update frequency, ensuring documentation reflects the current reality
- Recovery time actuals versus targets, comparing RTO commitments to performance
- Training completion rates across all staff levels
- Gap closure velocity shows how quickly identified weaknesses get addressed
- Audit findings trends demonstrating program maturity over time
Adapting to Emerging Threats
Monitor evolving risks like AI-driven cyberattacks, climate change impacts on operations, geopolitical supply chain disruptions, and regulatory expansion into operational resilience. Static programs become obsolete; dynamic ones incorporate threat intelligence feeds, scenario planning for emerging risks, and regular environmental scanning. Unique advantage: Automate audits with riskilience.com’s platform for real-time compliance monitoring rather than point-in-time assessments.
Partner with riskilience.com for ongoing program audits and optimization.
Integration with Enterprise Risk Management
Mature organizations recognize that business continuity doesn’t operate in isolation—it’s a critical component of comprehensive risk management. Integrate your BCM program with enterprise risk frameworks, information security initiatives, and operational resilience strategies. This enterprise risk management and business continuity integration creates unified visibility into organizational vulnerabilities and coordinated response capabilities.
Certification and Professional Development
Building program credibility often involves formal certification. ISO 22301 provides the globally recognized standard for business continuity management systems, offering structured frameworks and third-party validation. Investment in business continuity certification and pursuing credentials like Certified Business Continuity Professional elevates both organizational capabilities and individual expertise. Certified professionals bring standardized methodologies, industry best practices, and peer network access that accelerate program maturity.
The Role of Technology in Modern BCM
Technology enablement separates basic plans from sophisticated programs. IT business continuity requires specialized attention, given digital dependencies across all operations. Modern solutions include automated backup systems, cloud-based work-from-anywhere capabilities, communication platforms designed for crisis situations, and AI-powered risk monitoring that identifies threats before they materialize. Your IT business continuity plan should mirror organizational BCP structures while addressing technology-specific recovery requirements like system restoration sequences, data integrity verification, and cybersecurity during recovery operations.
Why Business Continuity Programs Matter More Than Ever
The question isn’t whether disruptions will occur; it’s whether your organization survives them competitively. Companies with robust continuity programs demonstrate measurable advantages: faster recovery following incidents, reduced revenue losses during disruptions, enhanced stakeholder confidence, improved regulatory compliance, and competitive differentiation in risk-conscious markets. Understanding why business continuity is important transforms it from a compliance checkbox to a strategic imperative.
Business continuity vs disaster recovery represents a critical distinction—DR focuses narrowly on technology restoration while BC addresses holistic organizational resilience, including facilities, personnel, suppliers, and customer relationships. Similarly, business resilience vs business continuity elevates thinking from survival (continuity) to adaptation and growth through adversity (resilience). Leading organizations pursue both.
Conclusion: Building Lasting Resilience
Implementing an effective business continuity program requires sustained commitment, adequate resources, and cultural integration beyond documentation exercises. Start with clear program objectives aligned to business goals, build comprehensive impact analysis identifying what truly matters, develop cost-justified strategies matched to actual risks, document actionable procedures eliminating ambiguity, test relentlessly to build confidence, and maintain through systematic reviews.
The most sophisticated programs treat continuity as ongoing capability development rather than compliance obligation. They leverage technology for efficiency, pursue certification for credibility, integrate with enterprise risk frameworks for coherence, and continuously adapt to emerging threats. Organizations that excel at business continuity don’t just survive disruptions—they emerge stronger, capturing market share from less-prepared competitors.
Ready to transform your continuity posture? Riskilience.com provides the expertise, tools, and frameworks that turn continuity theory into operational reality. Whether you’re building programs from scratch, seeking certification guidance, or optimizing mature capabilities, specialized support accelerates your journey toward genuine resilience. Don’t wait for the next disruption to expose gaps start building unshakeable continuity today.
